During the past month I spend a lot of time improving RIPS – my static analysis tool for PHP vulnerabilities. You can download the new version 0.40 here. In this post I will give a short project status report.
Whats new
There has been a couple of bugfixes and improving especially regarding file inclusions which are vital for correct analysis. Also RIPS now tries to analyse SQL queries on quotes before a decision on correct securing is made. However this feature is still not 100% working correctly in all cases.
// safe
$name = mysql_real_escape_string($_GET['name']);
mysql_query("SELECT * FROM users WHERE name = '$name'");
// vulnerable
$id = mysql_real_escape_string($_GET['id']);
mysql_query("SELECT * FROM users WHERE id = $id");
The main new visible features are graphs. Besides the list of all scanned files RIPS now gives a nice overview on how files are connected to eachother, what files accept sources (userinput) and what files have sensitive sinks or vulnerabilities. It also splits the scanned files in main files (blue) and included files (red) so that entry points can be spotted easily.
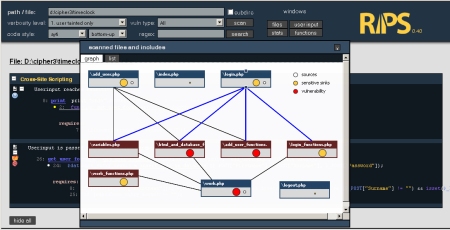
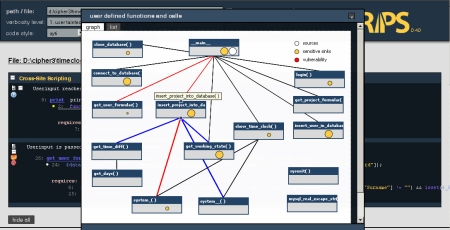
Also all function calls are visible in a connected graph. Red lines are highlighting the code flow of each vulnerability. With these features it is very easy to spot in which file a vulnerability exists and which functions have to be called to reach the sensitive sink before you actually look at the code.
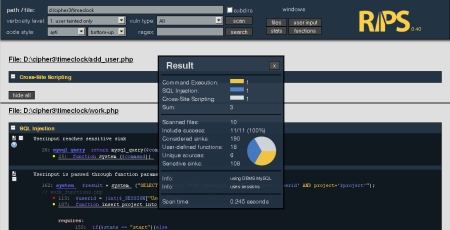
Another important feature is that code snippets that belong to the same vulnerability are now grouped and titled with the vulnerability category. In earlier versions they were unconnected and one had to jump between several snippets. With this it is now possible to look at specific vulnerability categories and to hide unimportant ones. This can be done by clicking on the categories name in the statistics window that also has been improved with a pie chart (HTML5 for the win ;)).
Also a new vulnerability type “Unserialize / POP” has been added that allows you to search for unserialize() sinks and interesting POP gadget functions (more info here). For more changes have a look at the changelog.
Whats missing
The main drawback of RIPS is still the missing support of Object-Oriented Programming (OOP). That means that almost all large code projects can not be scanned sufficiently and vulnerabilities will not be detected correctly. RIPS also still has problems with large non-OOP projects with complicated include structures. The new version improves the include strategie a lot, however if the filename is fetched from a database or build over several userdefined functions it is hard to reconstruct a string with static analysis. Also, a big block on my todo-list includes several bugs with the detection of proper and inproper securing that is also hard to detect with static analysis. So RIPS 0.40 remains being a good tool for small to bigger non-OOP apps but fails if you seriously want to scan WordPress or phpBB.
Whats coming
Scanning large OOP apps is still the main goal. After fixing currently known bugs (which are decreasing but finally increasing again every day ;)) it will be time for implementing basic OOP features. At the same time a complete rewrite is planned to improve development and contain new bugs. Also some basic behavior of RIPS needs to be changed to detect vulnerabilities more correctly. This includes the line-by-line reading which should be replaced by codeblocks and the handling of different data types, especially arrays. There has been some interests lately for a joint development so I am looking forward to how RIPS will evolve.
If you are aware of a bug in the new version or have a feature request please leave a comment or issue a request at sourceforge.



 Posted by Reiners
Posted by Reiners 



