PHP Scanner
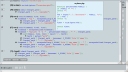
This little tool scans PHP Scripts for potential vulnerable PHP functions and then traces back its parameters. With this you can easily see if a parameter of a vulnerable function comes from userinput. Additionally PHP Scanner allows you to mark those lines in the source (bottom frame) and build custom CURL code to exploit the issues found.





(new and open source version: see RIPS)
RIPS – A static source code analyser for vulnerabilities in PHP scripts
Finally I improved the code from my old PHP Scanner and the new tool called RIPS was released during the Month of PHP Security. RIPS is open source and freely available at http://sourceforge.net/projects/rips-scanner/.
Some features:
- detect XSS, SQLi, File disclosure, LFI/RFI, RCE vulnerabilities and more
- 5 verbosity levels for debugging your scan results
- mark vulnerable lines in source code viewer
- user-defined function code by mouse-over on detected call
- list of all user-defined functions and program entry points (user input) connected to the source code viewer
- create CURL exploits for detected vulnerabilties with few clicks
- 7 different syntax highlighting colour schemata
- only minimal requirement is a local webserver with PHP and a browser (tested with Opera and Firefox)
Please note that due to its missing support of OOP code and data flow analysis, the development was abandoned in 2013 and a complete new generation was developed that is available at RIPS Technologies.


Hi Johannes Dahse! Thank you for new release RIPS and comment me in CHANGELOG. It is very useful tools. I found some vulnerabilities in my site by RIPS. I will be glad to assist your project.
Hi Johannes,

would you mind to give a look and review my ‘special’ SQLi framework? I do think you will find it …very useful, and maybe you could suggest me how to improve it.
It’s at Woodmann for now, because I dont have the time to make a site for it… maybe later in future.
You can see a screenshot here to quickly understand what it is made and thought for..
(on Woodmann’s CISTL http://www.woodmann.com/collaborative/sectools/index.php/SiAF_-_SQLi_Attack_Framework )
good job!